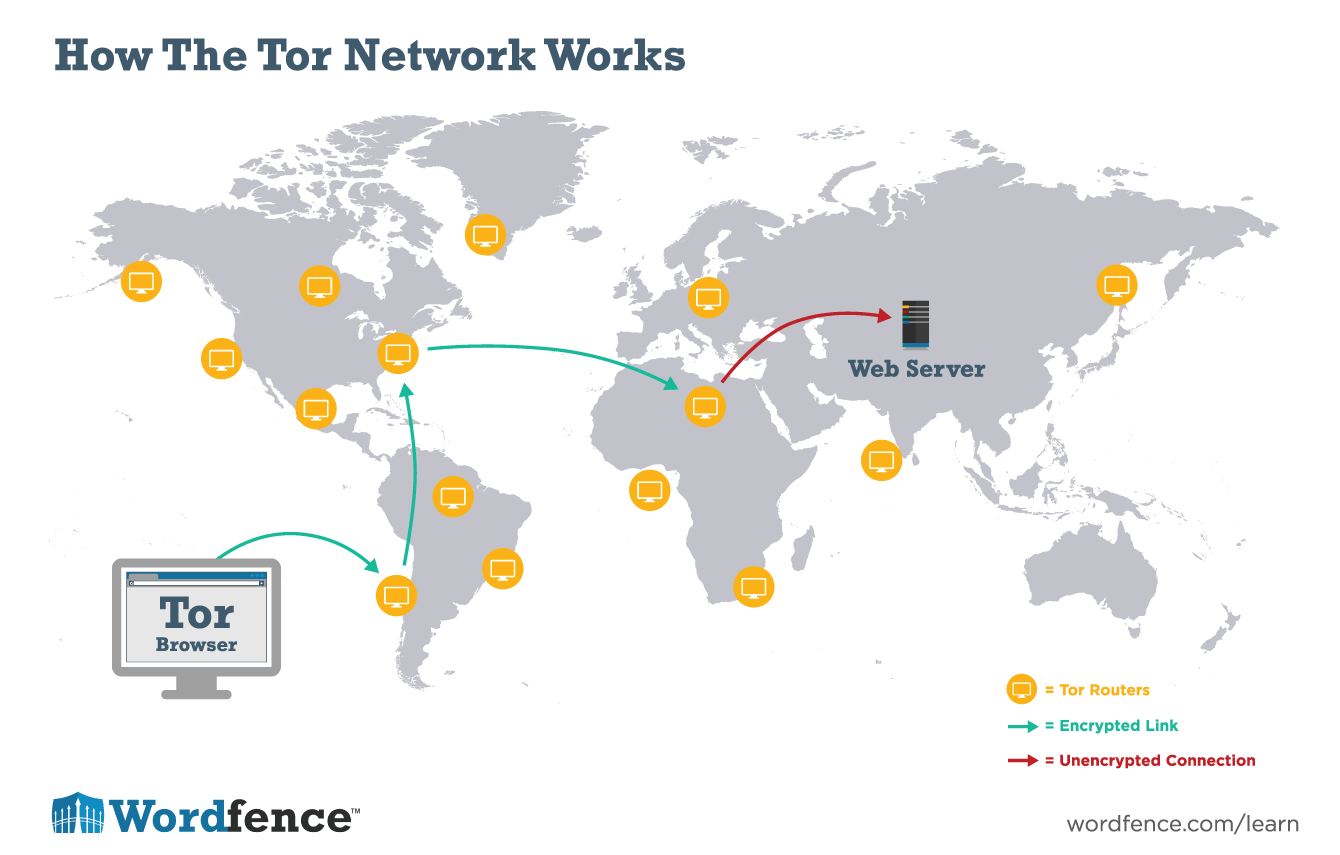
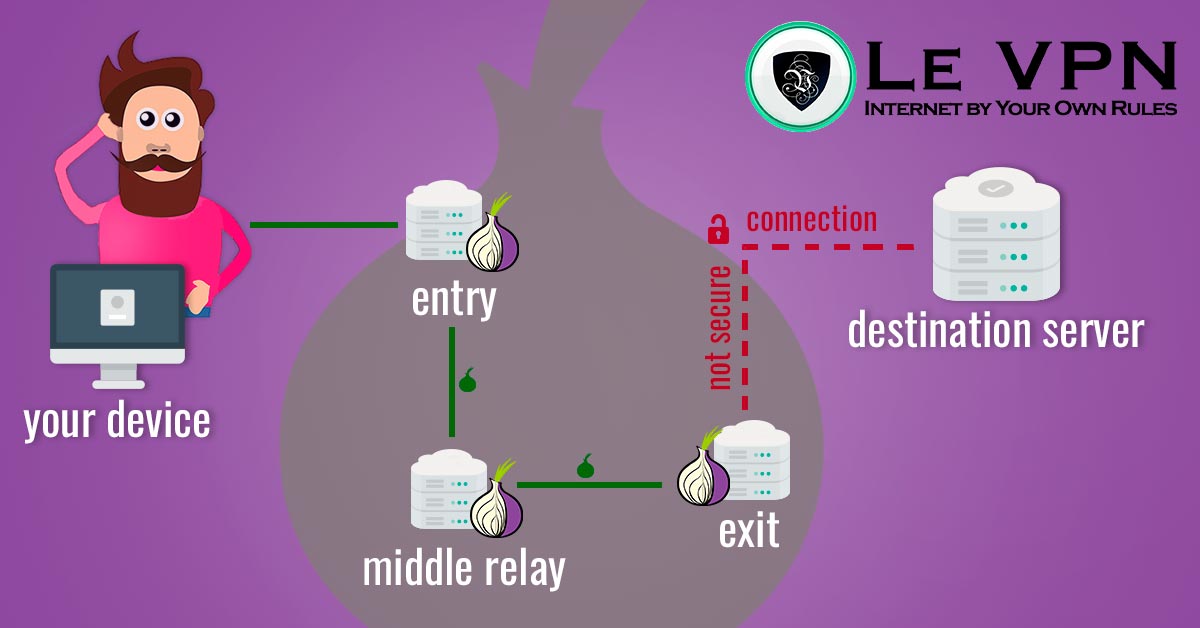
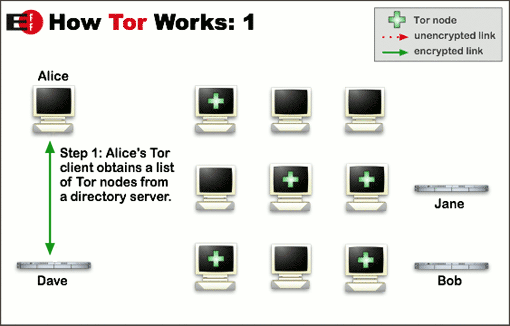
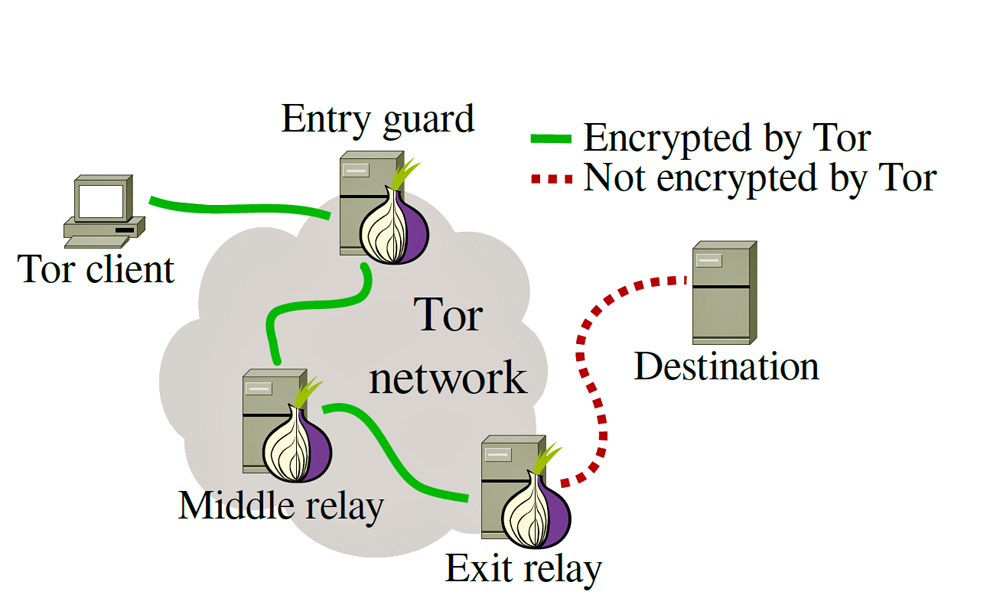
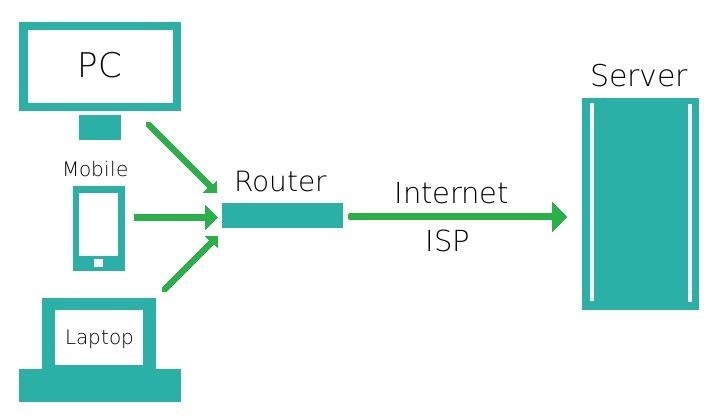
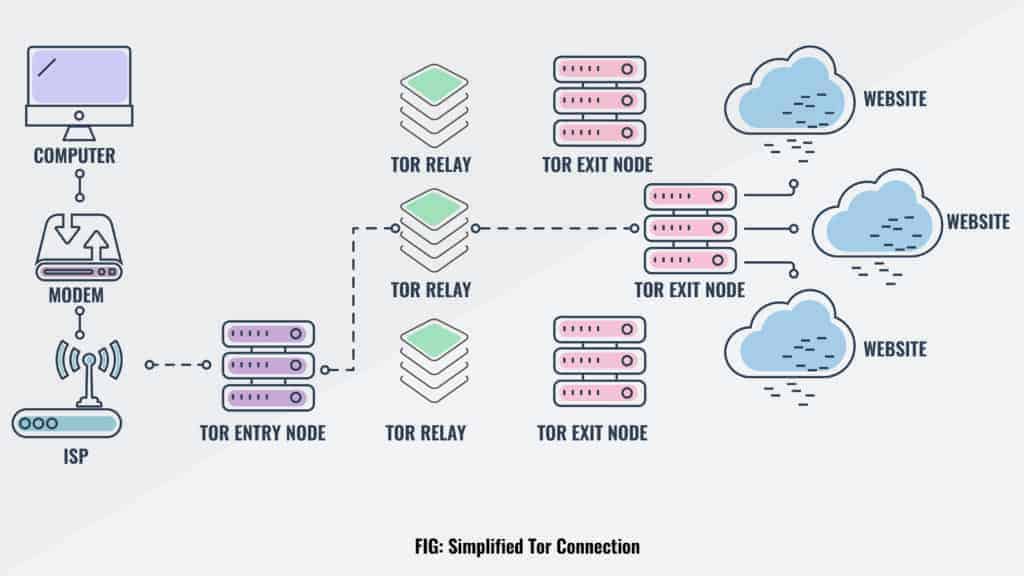
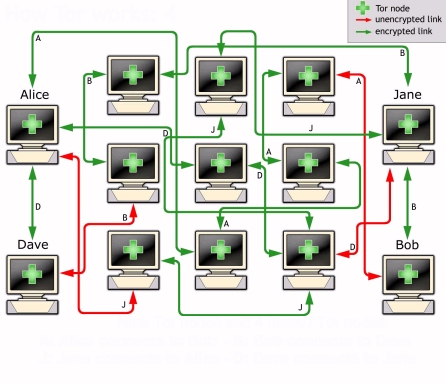
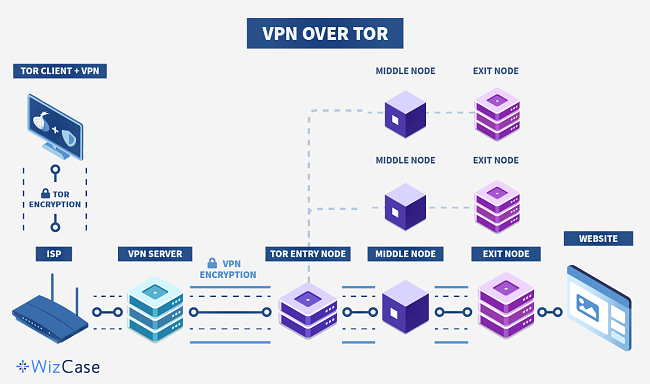
GitHub - chriswayg/tor-server: An efficient and secure Tor relay server Docker image based on Debian

What is the Differences between TOR and TOR Switch? - Knowledge - Shenzhen Optico Communication Co.,Ltd.

What is the difference between a directory server and a hidden service database? - Tor Stack Exchange