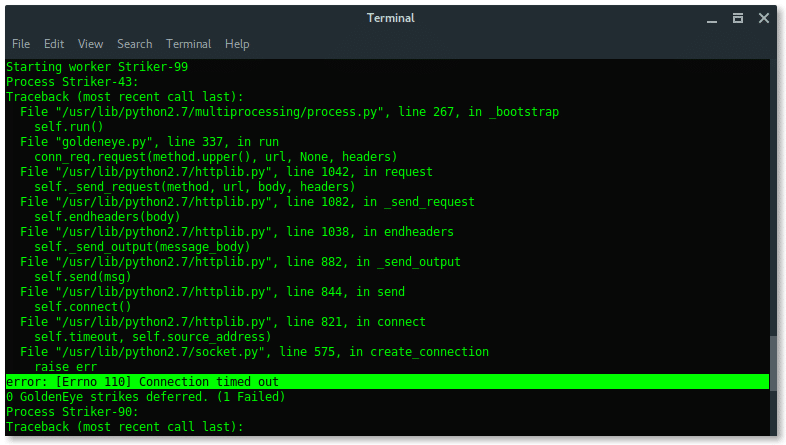
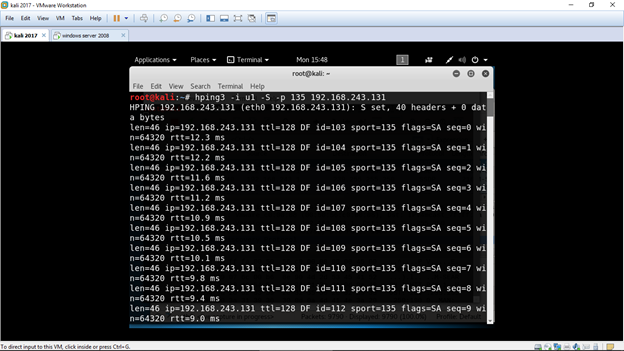
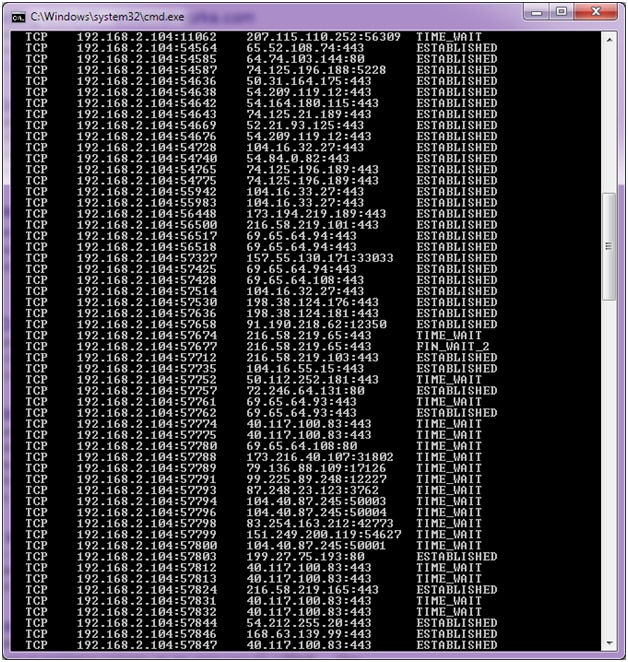
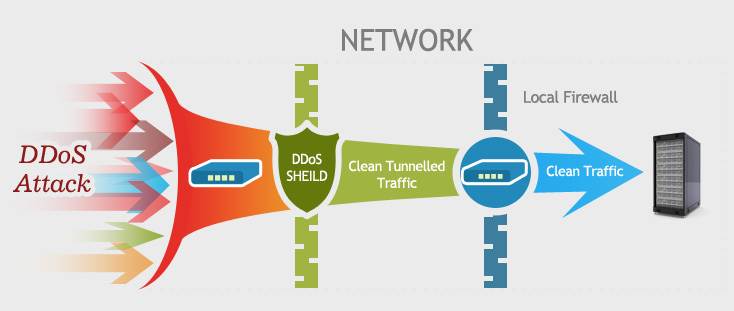
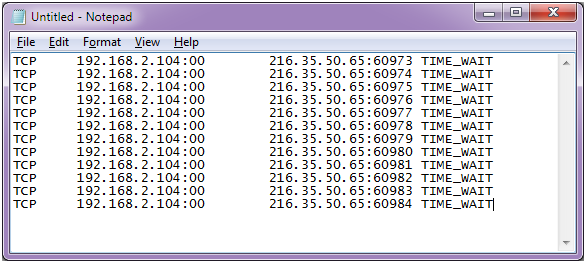
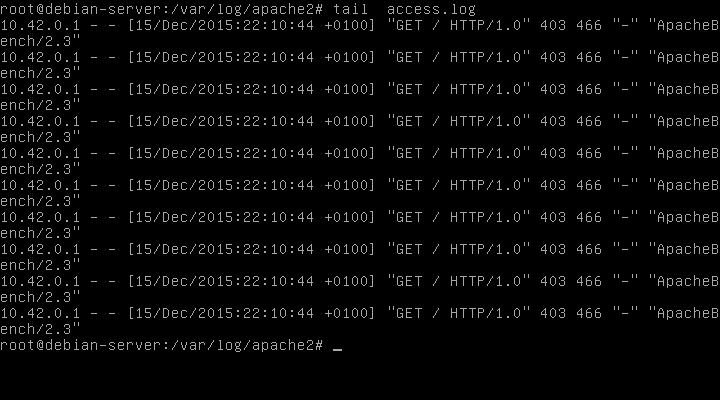
How to quickly check to see if your Linux server is under a DoS attack from a single IP address – Nasni Consultants

How to quickly check to see if your Linux server is under a DoS attack from a single IP address | TechRepublic

2017 DDoS and Web Application Attack Landscape - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.